Enabling Volume Encryption
In Catalogic vStor, you can improve data security by enabling encryption for a volume during its creation. To do so, switch on the Enable encryption toggle and define an Encryption Key. The Key must be between 15 and 128 characters in length.
Important. If encryption is enabled during volume creation, it cannot be disabled, meaning the data on the volume will remain encrypted.
When encryption is enabled, vStor uses the default ZFS encryption algorithm: aes-256-gcm. A Data Encryption Key (DEK) is generated to encrypt the volume. The user-defined Encryption Key serves as a Key Encryption Key (KEK), which encrypts the DEK. This design allows the user to change their Encryption Key (KEK) without having to decrypt and re-encrypt the entire volume.
Note. Any replica of the encrypted volume will also be encrypted with the same DEK, which is transferred to the partner vStor as part of the replication process. To decrypt the DEK, and ultimately the replicated volume, the user needs to provide the Encryption Key (KEK) they have defined for the original volume.


Optionally, enable Save key in Encryption Keystore to store the key securely in a remote location.
See more. To learn more about storing and managing encryption keys, see Using Remote Keystore.
Once encryption is enabled, you can lock or unlock your volume from its details page. Unlocking the volume means the Data Encryption Key (DEK) is loaded to the machine’s memory, allowing vStor to access the data without prompting the user for the Encryption Key (KEK) each time.
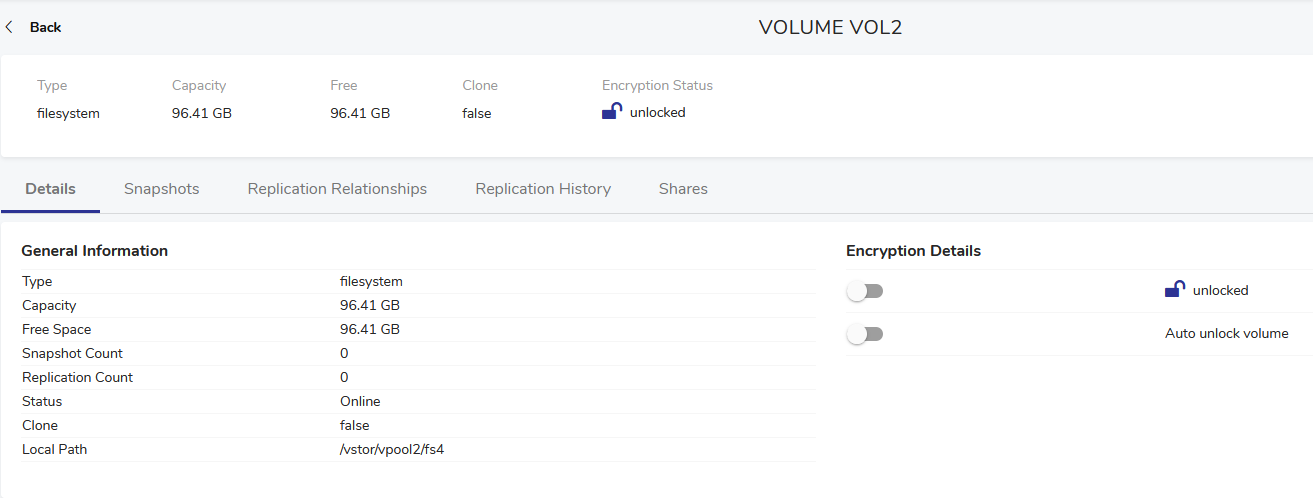
Attention! It is important to keep your Encryption Key safe, as it cannot be reset.
Last updated